picoCTF 2023 – findme
28 March 2023 – Written by Valentin Huber – in base64, ctf, curl, cyberchef, and web
Challenge
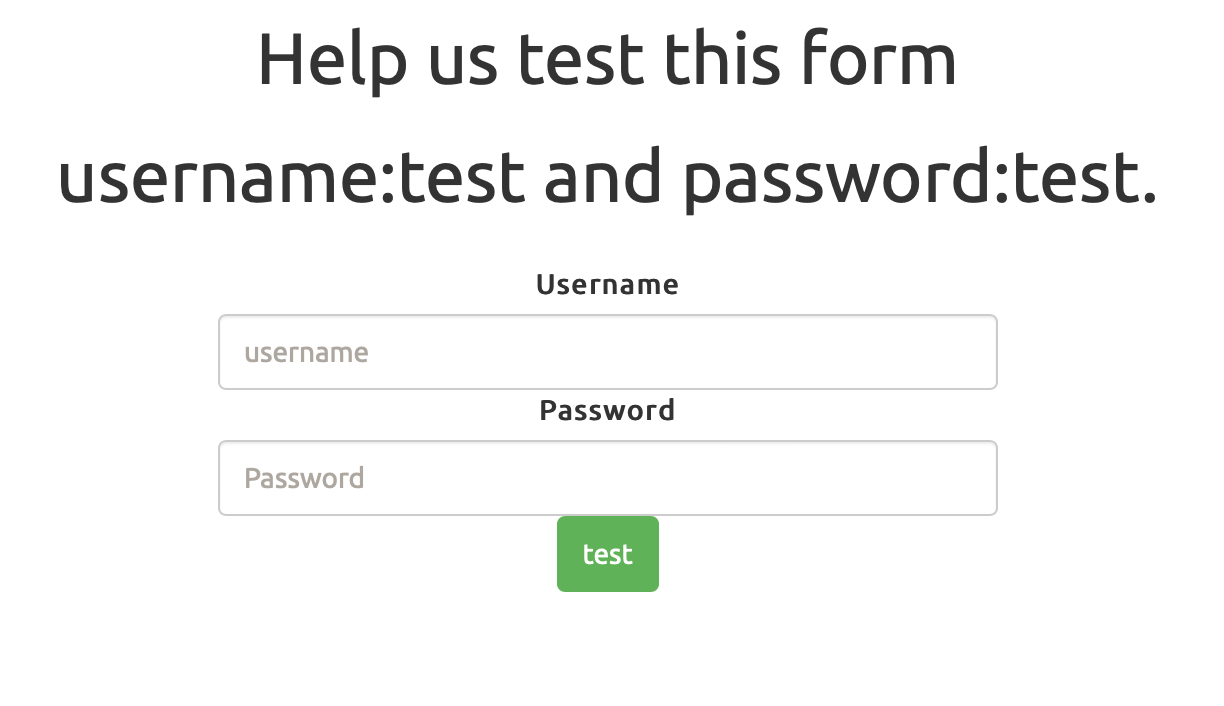
Help us test the form by submiting the username as
testand password astest!
Screenshot of the website:
After logging in with the provided username and password:
Solution
When logging in, you get redirected multiple times. So I manually checked each of the steps, starting with logging in:
curl -d "username=test&password=test\!" "[url]/login"
This returned:
Found. Redirecting to /next-page/id=cGljb0NURntwcm94aWVzX2Fs
So I checked that page:
curl "[url]/next-page/id=cGljb0NURntwcm94aWVzX2Fs"
And got:
<!DOCTYPE html>
<head>
<title>flag</title>
</head>
<body>
<script>
setTimeout(function () {
// after 2 seconds
window.location = "/next-page/id=bF90aGVfd2F5X2EwZmUwNzRmfQ==";
}, 0.5)
</script>
<p></p>
</body>
The == in the end of that id indicated base64, so I threw it into cyberchef and got l_the_way_a0fe074f}, which seemed like the second half of the flag. So I prepended the id of the first redirect and got picoCTF{proxies_all_the_way_a0fe074f}.